F5 Waf Icon
Advanced Web Application Firewall Waf F5
F5 Professional Services Sales Irule Icontrol Development Worldtech It
F5 Security Solutions Available And Secure Apps Anywhere
F5 Big Ip Ltm Initial Configuration Step By Step Guide

Installing F5 Big Ip Adc For Anthos Clusters On Vmware Using Manual Load Balancing
Q Tbn And9gcs3tukskmn1zkcgjhowlimggguwpgwytv Y34ljnqu Usqp Cau
Activate F5 product registration key Ihealth Verify the proper operation of your BIGIP system F5 University To add comments about the suggestion and the cause, click the Add Comment icon and type the comments Decide how to respond to the suggestion.
F5 waf icon. A web application firewall (WAF) protects the application layer and is specifically designed to analyze each HTTP/S request at the application layer It is typically user, session, and application aware, cognizant of the web apps behind it and what services they offer. Imperva WAF is a key component of a comprehensive Web Application and API Protection (WAAP) stack that secures from edge to database, so the traffic you receive is only the traffic you want We provide the best website protection in the industry – PCIcompliant, automated security that integrates analytics to go beyond OWASP Top 10 coverage, and reduces the risks created by thirdparty code. If a web application firewall (WAF) is in use, the application gateway checks the request headers and the body, if present, against WAF rules This action determines if the request is valid request or a security threat If the request is valid, it's routed to the backend If the request isn't valid and WAF is in Prevention mode, it's blocked as.
– A free PowerPoint PPT presentation (displayed as a Flash slide show) on PowerShowcom id 3f0e07ZDM2M. F5 Web Application Security Radovan Gibala Senior Solutions Architect rgibala@f5com 4 731 137 223 09 Agenda Challenge Websecurity What are the problems?. On the Add a Web Application Firewall blade, click Create New and then click F5 Networks On the Choose package blade, click F5 Networks Semiautomatically provisioned At the bottom of the F5 WAF Solution blade, click Create Continue with Configure the F5 WAF solution template Launching the WAF from the Azure Marketplace.
Azure Cloud WAF service from Radware is the only partner service running natively in Azure and utilizing the Azure Network This provides an application firewall service at ultralow latency, at proximity to your origin servers, with minimal impact on your web application performance. By implementing F5 Advanced WAF between applications and end users, businesses can decrypt and inspect all traffic before it enters the network or reaches the server in the cloud The WAF will then use advanced detection and mitigation techniques to prevent customer data from being accessed, manipulated, or stolen. An application firewall is a form of firewall that controls input/output or system calls of an application or service It operates by monitoring and blocking communications based on a configured policy, generally with predefined rule sets to choose from The application firewall can control communications up to the application layer of the OSI model, which is the highest operating layer, and.
The Symantec WAF App For Splunk provides several dashboards to render data from WAF logs and general ProxySG The dashboards provide visual charts and graphs to display attack families, malware information, engines (including engine parts and rules) and other blocked or monitored details Exclusive to this app is the feature to filter. Azure Web Application Firewall (WAF) on Azure Application Gateway provides centralized protection of your web applications from common exploits and vulnerabilities Web applications are increasingly targeted by malicious attacks that exploit commonly known vulnerabilities SQL injection and crosssite scripting are among the most common attacks. This reference architecture shows a secure hybrid network that extends an onpremises network to Azure The architecture implements a DMZ, also called a perimeter network, between the onpremises network and an Azure virtual networkAll inbound and outbound traffic passes through Azure Firewall.
131 Open Visual Studio Code by clicking on the icon shown below¶ 132 Once Visual Studio Code is open, you’ll see a collection on the left titled ‘UDF_WAF_CICD’ with several items underneath 134 Click on ‘secops_waf_policy_1json’ and review the configuration of the file 1 Import into the BIGIP 2 Navigate to ‘Security ›› Application Security Security Policies. Get free icons of Desktop application in Windows 10 style for your design The free images are pixel perfect and available in png and vector Download icons in all formats or edit them for your designs As well, welcome to check new icons and popular icons. AAG includes a web application firewall called Web application firewall (WAF) that protects your workload from common exploits like SQL injection attacks or crosssite scripting attacks, to name a few This protection uses rules from the Open Web Application Security Project version 30 or 229 However, it is not an L3L7 stateful firewall.
Activate F5 product registration key Ihealth To add comments about the suggestion and the cause, click the Add Comment icon to the right of the suggestion commands, and type the comments Decide how to respond to the suggestion You can start with the suggestions that have the highest learning scores, or those which you know to be valid. Web Application Firewall (WAF) with Azure Front Door and CDN Pricing 1 WAF pricing includes monthly fixed charges and request based processing charges There is a monthly charge for each policy and addon charges for Custom Rules and Managed Rulesets as configured in the policy. Web Application Firewall Market Size, Share, Trends Analysis Report 25 The report has categorized the market based on deployment, organization size, service and end use industry The competitive landscape of the market has also been analyzed in the report with the detailed profiles of the key players.
F5 Web Application Security Radovan Gibala Senior Solutions Architect rgibala@f5com 4 731 137 223 09 Agenda Challenge Websecurity What are the problems?. F5 Web Application Firewall Solutions > Class 8 F5 Advanced WAF 141 > Module – Threat Campaigns Source PDF Testing Threat You can get more details about the Threat Campaign from within this screen by clicking on the icon next to the Threat Campaign name. The F5 Advanced WAF administrator can control the blocking of Threat Campaigns in two locations;.
FortiADC Web Application Firewall can detect a zero day attack and protect from OWASP top10 and many other threats with multivector protection such as SQLi and XSS Protection, Web Scraping, Brute Force, Web Defacement, Protocol Validation (HTTP RFC) and Web Attack Signature using FortiGuard WAF Security Services for layer 7 attacks (subscription required). FortiWeb Cloud WAFasaService is a SecurityasaService (SaaS) cloudbased web application firewall (WAF) that protects public cloud hosted web applications from the OWASP Top 10, zeroday threats, and other application layer attacks. A WAF or Web Application Firewall helps protect web applications by filtering and monitoring HTTP traffic between a web application and the Internet It typically protects web applications from attacks such as crosssite forgery, crosssitescripting (XSS), file inclusion, and SQL injection, among othersA WAF is a protocol layer 7 defense (in.
AWAF Lesson 14 – Behavioral DoS Protection F5 WWFE Lab Guide – BIGIP ASM/Adv WAF Full Course, Partner Edition, v131B Page 105 Exercise – Use Behavioral DoS Protection • Estimated completion time 60 minutes Task 1 – Create a Security Policy and DoS Profile Create a security policy for test_site_virtual, and then configure a DoS profile for test_site_virtual using behavioral DoS. Multiple designs of icons for any type of presentation, background, and document If you are a Fortinet partner or user, you will find many Fortinet specific technology and product icons as well many of which can be easily used in a more generic setting as well. Compare the best DevOps software that Integrates with Gitpod of 21 for your business Find the highest rated DevOps software that Integrates with Gitpod pricing, reviews, free demos, trials, and more.
The BIGIP ® dashboard displays system statistics in selectable graphs, gauges, and tables In addition to the predefined views, you can create custom combinations of the dashboard windows, called views, and save them in groups, called view setsYou can combine windows from different BIGIP modules in a single view, or use just the windows you want for a single module. Multiple designs of icons for any type of presentation, background, and document If you are a Fortinet partner or user, you will find many Fortinet specific technology and product icons as well many of which can be easily used in a more generic setting as well. Monthly updates with new products, network elements, and other icon families;.
Azure Web Application Firewall (WAF) on Azure Application Gateway provides centralized protection of your web applications from common exploits and vulnerabilities Web applications are increasingly targeted by malicious attacks that exploit commonly known vulnerabilities SQL injection and crosssite scripting are among the most common attacks. Advanced Web Application Firewall (WAF) Protect your apps with behavioral analytics, proactive bot defense, and applicationlayer encryption of sensitive data Use the ROI Estimator from F5 and Forrester to find out how Advanced WAF can improve your security posture and save you money. 1 Open Local Traffic > Virtual Servers and click on webgoatf5democom_https_overlay_vsGo to the Resources horizontal tab and verify that the iRule webgoat_overlay is applied Freel free to check out the code in the iRule This code and BIGIP flexibility makes lab testing and simulations a breeze Modify the cURL command to point at the overlay virtual server and run several times curl.
Web Application Firewall Market Size, Share, Trends Analysis Report 25 The report has categorized the market based on deployment, organization size, service and end use industry The competitive landscape of the market has also been analyzed in the report with the detailed profiles of the key players. AAG includes a web application firewall called Web application firewall (WAF) that protects your workload from common exploits like SQL injection attacks or crosssite scripting attacks, to name a few This protection uses rules from the Open Web Application Security Project version 30 or 229 However, it is not an L3L7 stateful firewall. The file archiving solution for servers and network storage systems that lets you use any device as second tier storage Featuring a tiny footprint on the host system along with full support for cloud, DFS, replication, deduplication, and compression ArchiverFS lets you use any NAS, SAN or cloud platform as storage for your old unstructured files.
Dublin, Dec 07, (GLOBE NEWSWIRE via COMTEX) Dublin, Dec 07, (GLOBE NEWSWIRE) The "Greater China Web Application Firewall Solutions Market,. An application firewall is a form of firewall that controls input/output or system calls of an application or service It operates by monitoring and blocking communications based on a configured policy, generally with predefined rule sets to choose from The application firewall can control communications up to the application layer of the OSI model, which is the highest operating layer, and. Solution #ScopeThis solution applies to all Barracuda Load Balancer models 340 and above, running firmware versions 31 and above, using the Route Path or Bridge Path deployment with SSL OffloadingAnswerTo force all inbound HTTP requests for a service to HTTPS while using SSL offloading on the Load Balancer, two services must be created.
Compare the best Web Application Firewalls (WAF) of 21 for your business Find the highest rated Web Application Firewalls (WAF) pricing, reviews, free demos, trials, and more. Recently, I had the opportunity to participate in a podcast with the team at F5 Christine Puccio – VP of Global Cloud Alliances and Heath Parrott – Senior Global Solutions Architect for Cloud discussed their latest announcement the integration between F5 Essential App Protect, a web application firewall (WAF) SaaS solution and Amazon CloudFront, a content delivery network (CDN) solution. By implementing F5 Advanced WAF between applications and end users, businesses can decrypt and inspect all traffic before it enters the network or reaches the server in the cloud The WAF will then use advanced detection and mitigation techniques to prevent customer data from being accessed, manipulated, or stolen.
Get free icons of Desktop application in Windows 10 style for your design The free images are pixel perfect and available in png and vector Download icons in all formats or edit them for your designs As well, welcome to check new icons and popular icons. A WAF or Web Application Firewall helps protect web applications by filtering and monitoring HTTP traffic between a web application and the Internet It typically protects web applications from attacks such as crosssite forgery, crosssitescripting (XSS), file inclusion, and SQL injection, among othersA WAF is a protocol layer 7 defense (in. Activate F5 product registration key Ihealth Verify the proper operation of your BIGIP system F5 University To add comments about the suggestion and the cause, click the Add Comment icon and type the comments Decide how to respond to the suggestion.
Accelerates adoption of the F5 Silverline WAF service for selected applications Delivered in collaboration with F5 Professional Services, this fixed price, fixed scope option provides both technical and project management resources to minimize the impact on your internal resources and to quickly and effectively deploy the Silverline WAF to your web application environments. Product Overview The F5 Web Application Firewall solution is delivered by F5's industryleading BIGIP Application Security Manager (ASM) and BIGIP Local Traffic Manager (LTM), providing advanced firewall capabilities by securing applications from layer 7 DDoS attacks, malicious bot traffic, common application vulnerabilities and all OWASP top 10 threats. To prevent brute force attacks, the Application Security Manager tracks the number of failed attempts to reach the configured login URLs The system considers it to be an attack if the failed logon rate increased at a very high rate or if failed logins reached a certain number.
– A free PowerPoint PPT presentation (displayed as a Flash slide show) on PowerShowcom id 3f0e07ZDM2M. AWS WAF is a web application firewall that helps protect your web applications or APIs against common web exploits that may affect availability, compromise security, or consume excessive resources AWS WAF gives you control over how traffic reaches your applications by enabling you to create security rules that block common attack patterns. This reference architecture shows a secure hybrid network that extends an onpremises network to Azure The architecture implements a DMZ, also called a perimeter network, between the onpremises network and an Azure virtual networkAll inbound and outbound traffic passes through Azure Firewall.
To display a general description of that type of violation, click the info icon to the left of the violation name By reviewing the highrated illegal requests, you can determine whether your application is being attacked and get an idea of where the attacks are coming from and what the attackers are doing. Application Gateway Standard_v2 and WAF_v2 SKU Azure Application Gateway Standard_v2 and WAF_v2 SKU offer additional support for autoscaling, zone redundancy, and Static VIP These gateways also offer enhanced performance, better provisioning, and configuration update time, Header rewrites, and WAF custom rules. Many network architects use Microsoft Visio to build easytoshare, presentationready diagrams of complex networks To help you map out the integration of F5 devices into your network, we provide professionalquality Visio stencils of all our BIGIP and VIPRION hardware.
When this setting is enabled, the system hides the password revealer icon on a web page, for browsers that use a password revealer icon (for example, Internet Explorer versions 10 and later) Note If you are using JavaScript Function for Substitute Values or Custom Encryption Function , you must enable Hide Password Revealer Icon. Regionally located support centers enable F5 to provide support in a number of languages through nativespeaking support engineers See more Contact Support North America or Outside North America Local Support Numbers Feedback and Help. When this setting is enabled, the system hides the password revealer icon on a web page, for browsers that use a password revealer icon (for example, Internet Explorer versions 10 and later) Note If you are using JavaScript Function for Substitute Values or Custom Encryption Function , you must enable Hide Password Revealer Icon.
Community Training Classes & Labs > F5 Web Application Firewall Solutions > Lab 22 Session Hijacking Protection Session hijacking is a class of attacks that allow an illegitimate user to take control of a legitimate session that was initiated by a legitimate user. Jan 04, 21 (SUPER MARKET RESEARCH via COMTEX) According to the latest report by IMARC Group, titled, "Web Application Firewall Market Global Industry. F5 regularly releases new updates for BIGIP ASM components The updates, known as Live Update files, depending on your version, include new attack signatures, behavioral WAF, browser challenges, credential stuffing, server technologies, bot signatures, and threat campaigns in addition to enhancements and revisions to existing components.
In Blocking Settings for the policy as a whole, and in Threat Campaigns to control individual threat campaign signatures Recall, from reviewing the Threat Campaign details previously, that individual threat campaign signatures can be Enforced or Disabled. To display a general description of that type of violation, click the info icon to the left of the violation name By reviewing the highrated illegal requests, you can determine whether your application is being attacked and get an idea of where the attacks are coming from and what the attackers are doing. Monthly updates with new products, network elements, and other icon families;.
Web Application Firewall allows you to configure request size limits within lower and upper bounds The following two size limits configurations are available The maximum request body size field is specified in kilobytes and controls overall request size limit excluding any file uploads This field has a minimum value of 1 KB and a maximum. A web application firewall (WAF) protects web applications from a variety of application layer attacks such as crosssite scripting (XSS), SQL injection, and cookie poisoning, among othersAttacks to apps are the leading cause of breaches—they are the gateway to your valuable data With the right WAF in place, you can block the array of attacks that aim to exfiltrate that data by. At some point I realized the logs were mostly filled with complaints about illegal URLs beginning with /appletouchicon So i found a way to suppress those This is for version 121 The problem Typical example from a typical WAF log The details LTM policy to suppress those entries How to edit policy These are policies in the Local Traffic.
Avi Networks Vs F5 Networks Avi Networks
Www Dynatrace Com Hub Detail F5 Big Ip Ltm
1

Sx8ntrkdikbfcm
Azure And F5 Waf In The Cloud Devcentral

Social Networks Psilva S Prophecies
Advanced Web Application Firewall Waf F5
Media Readthedocs Org Pdf F5 Agility Labs Waf Latest F5 Agility Labs Waf Pdf

Generating F5 Big Ip Application Security Manager Waf Rules From Netsparker Standard Netsparker
Nginx High Performance Load Balancer Web Server Reverse Proxy

F5 Networks Tmos Administration Study Guide By F5 Books Issuu

F5 Big Ip Virtual Edition Byol
F5 Archives Exclusive Networks Middle East

Deploying F5 S Web Application Firewall In Microsoft Azure Security Center
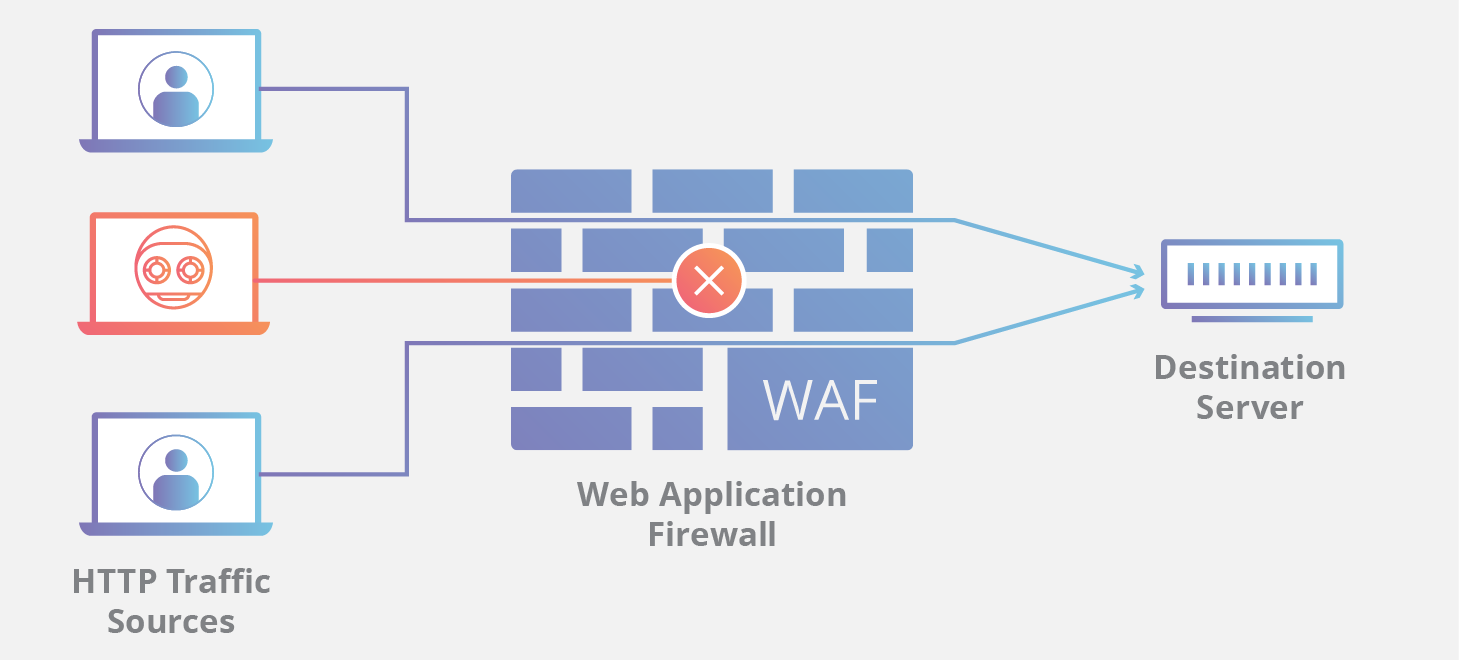
What Is A Waf Web Application Firewall Explained Cloudflare
1

Microsoft Psilva S Prophecies
Web Application Firewall Computer Security Information Security Firewall Icon Transparent Background Png Clipart Hiclipart
Application Security F5 Networks
Avi Networks Vs F5 Networks Avi Networks
Web Application Firewall 101 Learn All About Wafs

F5 Waf On Azure Security Center Youtube
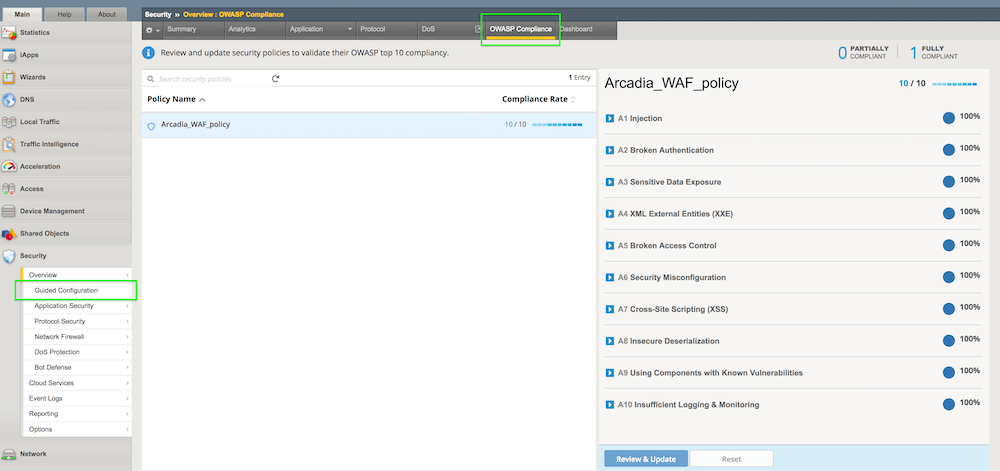
Sx8ntrkdikbfcm
F5 Advanced Web Application Firewall F5 Awaf Security
F5 Archives Exclusive Networks Middle East

Cloud Application Services Delivered On Demand F5

Cloud Application Services Delivered On Demand F5

Trend Micro Deep Security Ssl Traffic Inspection
F5 Archives Exclusive Networks Middle East
Web App And Api Protection Solutions F5
Web Application Firewall Icon Free Icons Library
Web Application Firewall Icon Free Icons Library

Barracuda Vs F5 Gartner Peer Insights 21
Web Application Firewall Icon Free Icons Library
Application Security F5 Networks

Installing F5 Big Ip Adc For Anthos Clusters On Vmware Using Manual Load Balancing
Q Tbn And9gcrhwzv8ex9ei9dgixvouff8p73yfioluqqbpkozjb8 Usqp Cau
F5 Networks Big Ip Cloud Edition Infradata
Index Of Wp Content Uploads 18 11

Visio Stencil For F5 Network Techbast
Media Readthedocs Org Pdf F5 Agility Labs Waf Latest F5 Agility Labs Waf Pdf

F5 Asm Lab 5 1 Rapid Deployment Policy Setup Youtube
Avi Networks Vs F5 Networks Avi Networks
F5 Professional Services Sales Irule Icontrol Development Worldtech It
Build And Deploy Scalable High Performing And Secure Apps F5
4 5 1 Create A Virtual Server On Big Ip Ve The Old Fashioned Way

F5 Networks Big Ip Diameter Traffic Management Appdeliveryworks Com

10 Best Web Application Firewalls Waf Vendors Reviewed In 21
Web App And Api Protection Solutions F5
Web Application Firewall Icon Free Icons Library

Big Ip F5 Or Load Balancer Ios Upgrade And Installation Direct 11 5 0 To 14 1 0 Youtube

Cloudflare Waf Web Application Firewall Cloudflare Uk
Create A Beacon Application F5 Cloud Services

Tmg2f5 Series Publishing Microsoft Exchange Using F5 Networking In The Windows World
Advanced Web Application Firewall Waf F5

F5 What Does It Take To Deploy A Web Application Firewall Why Are They Needed Get To Know F5 S Advanced Waf Launchpad Service T Co Ckppjgrri1 Appsec T Co Tk4uvfl0bm

Introduction To Ltm Dedicated To My Non Persian Languages Friends
F5 Advanced Web Application Firewall F5 Awaf Security
Managed Rules For Aws Waf Web Application Firewall

Waf Web Application Firewall 101 Load Balancers
Application Services F5
Application Security F5 Networks

F5 Big Ip Asm Waf Rules Report Netsparker
F5 Ltm Visio Icon Hd Png Download Vhv
Web App And Api Protection Solutions F5
Http Www Download Safeplus Pl Prezentacje Cisco secure 15 15 11 26 f5 networks Pdf

Shape Security Preventing Cyber Attacks

Cloud Application Services Delivered On Demand F5

F5 Big Ip Ve On Aws Quick Start
Nginx High Performance Load Balancer Web Server Reverse Proxy

F5 Solutions

F5 Professional Services Sales Irule Icontrol Development Worldtech It

Installing F5 Big Ip Adc For Anthos Clusters On Vmware Solutions
Advanced Web Application Firewall Waf F5

Askf5 Manual Chapter Planning A Big Iq Centralized Management Deployment

How To Validate F5 Big Ip Mobile App Anti Bot Configuration

Microsoft Sharepoint 16 Big Ip V11 4 V13 Ltm Apm Asm Afm m F5
Advanced Web Application Firewall Waf F5
Application Security F5 Networks
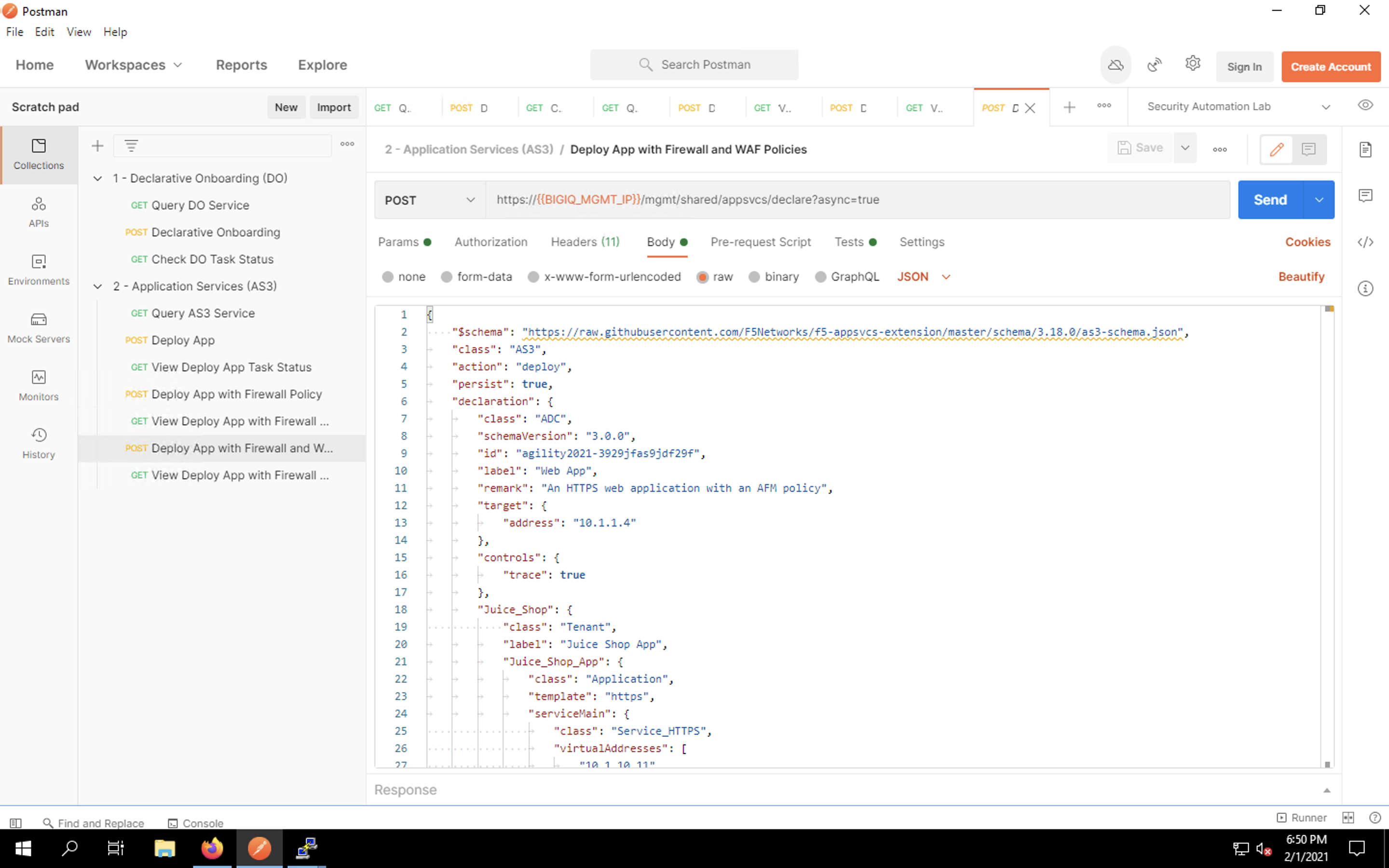
Web App With Firewall And Waf Policy Deployment

F5 Vs Imperva Gartner Peer Insights 21
F5 Advanced Web Application Firewall F5 Awaf Security

F5 Asm Lab 5 2 Assign An Application Security Policy To The Virtual Server Youtube

Sqreen Market Share And Competitor Report Compare To Sqreen F5 Big Ip Application Security Manager Sucuri Waf
F5 Networks Png And F5 Networks Transparent Clipart Free Download Cleanpng Kisspng
Lab 1 Dave Deploy App To Dev Environment F5 Rs Docs Latest Documentation
Web Application Firewall Icon Free Icons Library
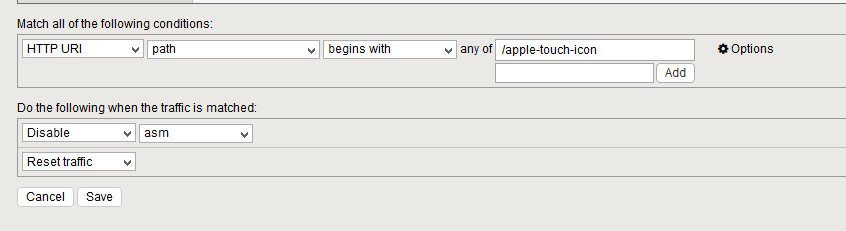
Suppress Apple Touch Icon Urls On An F5 Asm Dr John S Tech Talk

Web Application Firewall Aws Marketplace
F5 Networks Computer Icons Application Delivery Controller Application Delivery Network Shop Logo Computer Network Text Png Pngegg

F5 Irule Setup And Notes For Vmware Vcloud Director Accessibility Clouds Etc
Advanced Web Application Firewall Waf F5
Nginx High Performance Load Balancer Web Server Reverse Proxy
F5 Transparent Background Png Cliparts Free Download Hiclipart
Nginx High Performance Load Balancer Web Server Reverse Proxy
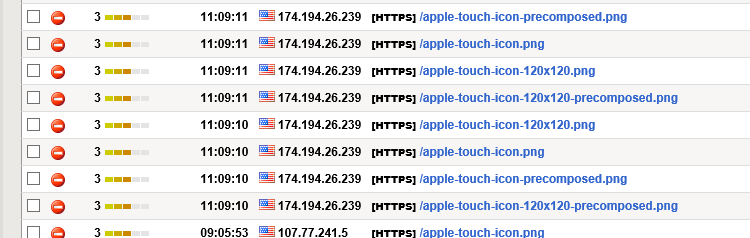
Suppress Apple Touch Icon Urls On An F5 Asm Dr John S Tech Talk

F5 Bigip Name Based Reverse Proxy Ltm Policies Somoit Net
F5 Multi Cloud Security And Application Delivery



